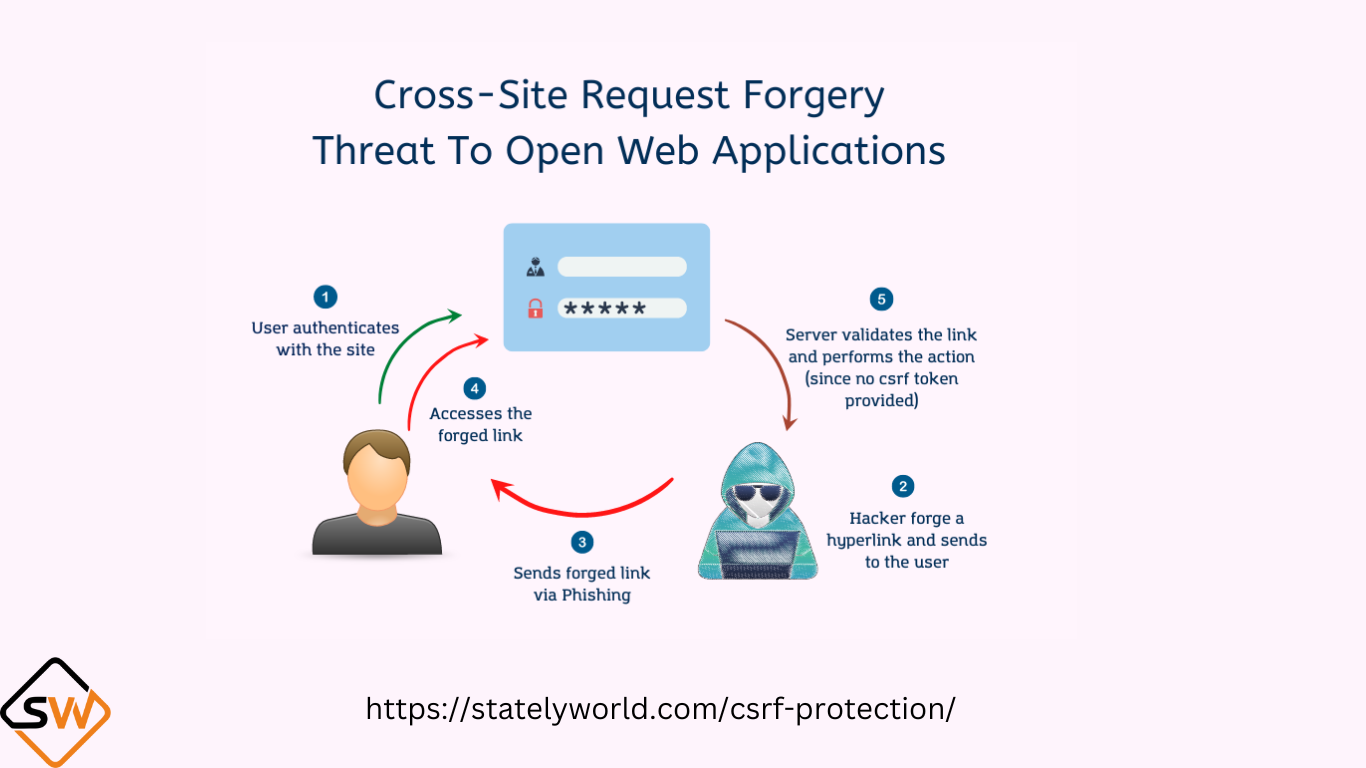
CSRF stands for Cross-Site Request Forgery. It is a security vulnerability that occurs when an attacker tricks a user into performing actions on a website without the user’s knowledge or consent. CSRF attacks are possible when a web application does not properly validate or authenticate requests.
How CSRF Attacks Work:
An attacker creates a malicious website or email containing a link or form that sends a request to a target website where the user is already authenticated. The user, while logged into the target website in the same browser, visits the malicious website or clicks on the link. The malicious website or link triggers a request (e.g., changing email or password, making a financial transaction) on the target website without the user’s knowledge or consent. Since the user is authenticated on the target site, the request is executed as if it were genuinely initiated by the user.
CSRF Protection:
To prevent CSRF attacks, web applications use various security mechanisms, including:
- CSRF Tokens: Most commonly, web applications generate unique tokens for each user session. These tokens are embedded in forms or included in headers for every request. The server checks the token to verify the authenticity of the request. Since attackers cannot obtain these tokens, they can’t craft malicious requests.
- Same-Site Cookies: Setting the “SameSite” attribute on cookies can help restrict how cookies are sent in cross-site requests, preventing unauthorized requests from external websites.
- Double-Submit Cookies: In addition to session tokens, some web applications use a separate token stored in a cookie to compare with the token submitted in the request. This is an added layer of protection.
- Custom Headers: Some applications use custom HTTP headers to identify and validate requests.
CSRF protection is crucial because it prevents attackers from forcing users to perform actions they didn’t intend to on web applications. Without proper CSRF protection, attackers can exploit user trust and authenticated sessions to manipulate user accounts, change settings, or perform actions that could lead to serious security breaches or data loss.
Web developers should implement CSRF protection in their applications to safeguard user data and ensure the integrity of actions performed within their systems. Most web development frameworks provide built-in support for CSRF protection, making it easier for developers to implement these security measures.
Using CSRF Protection in Laravel
1. Verify CSRF Token in Forms:
Laravel automatically generates and includes a CSRF token in every form created using the @csrf Blade directive. For example, in your HTML form, you can include it like this:
<form method="POST" action="/example">
@csrf
<!-- Other form fields and buttons -->
</form>
This token will be automatically validated when the form is submitted, ensuring that the request is legitimate.
2. CSRF Middleware:
Laravel’s VerifyCsrfToken middleware automatically checks the CSRF token on incoming POST, PUT, and DELETE requests. You don’t need to manually add this middleware; it’s included by default in the global middleware stack.
3. Custom Middleware:
You can also apply CSRF protection to specific routes or groups using middleware. For example, you can create a custom middleware group in your app/Http/Kernel.php file and add it to the routes you want to protect:
protected $middlewareGroups = [
'web' => [
// ...
\App\Http\Middleware\VerifyCsrfToken::class,
// ...
],
// ...
];
4. Excluding Routes:
If you have specific routes that you want to exclude from CSRF protection, you can add them to the $except property in the VerifyCsrfToken middleware located in the app/Http/Middleware directory.
protected $except = [
'example/some-route',
];
Be cautious when excluding routes from CSRF protection, as this should only be done for routes that are safe from CSRF attacks.
5. API Routes:
If you are building an API using Laravel, CSRF protection is generally not used since API endpoints are typically stateless. You can exclude CSRF protection for API routes by excluding them from the web middleware group.
In your app/Http/Kernel.php file, you can create a custom middleware group for your API routes.
protected $middlewareGroups = [
'api' => [
'throttle:60,1',
'bindings',
// ...
],
];
API routes in Laravel use the api middleware group, which doesn’t include CSRF protection.
By following these steps, you can effectively use CSRF protection in your Laravel application to prevent CSRF attacks and enhance the security of your web forms and routes. Laravel’s built-in CSRF protection makes it easy to secure your application against these types of attacks without much effort on your part.





