What is Cyber Security and How to build a successful career in it?
What is Cyber Security and How to build a successful career in it?

Cyber Security, Ethical Hacking, Network Security are some words which commonly searched by the user in the google.
This article on “What is Cyber Security and how do I build a career in it? Before we talk about a career in it, we will know what is cyber security? According to Wikipedia
“Computer security, Cyber security or Information Technology security is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide“.
Security is used on a variety of computer networks, both public and private, to secure daily transactions and communications among businesses, government agencies and individuals.
The Different types of Cyber Security Threats/Attacks
- CSRF (Cross-site request forgery) Attack
- Password Attack (Two factor authentication)
- SQL Injection Attack
- Malware
- Phishing Attacks
- Man-in-the-middle (MitM) Attack
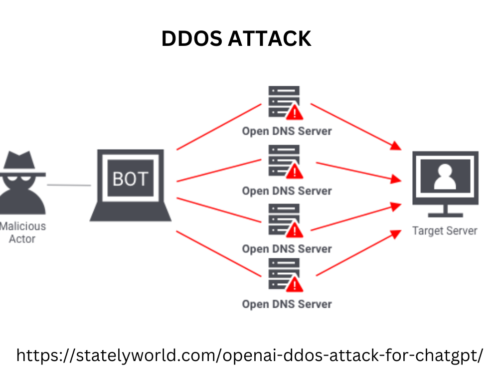
- Denial-of-service (DoS) Attacks
- WannaCry ransomware attack
Note:The WannaCry ransomware attack was a May 2017 worldwide cyberattack by the WannaCry ransomware cryptoworm, which targeted computers running the Microsoft Windows operating system by encrypting data and demanding ransom payments in the Bitcoin cryptocurrency. Know more
So in general terms, you can say that cyber security is important to protect against these attacks. Now the question comes in mind, who does these attacks?
Cyber attacks against businesses are often deliberate and motivated by financial gain. However, other motivations may include:
- Hactivism (To promote a political agenda or social change)
- Cyber Espionage – eg spying on competitors for unfair advantage
- Intellectual challenge – eg ‘white hat’ hacking
- Cyber Crime
- Cyber War
Best computer security practices.
1. Install and maintain updated anti-virus and anti-spyware software at desktop level.
2. Scan computer system with updated anti-virus for possible infections and disinfect the same.
3. Install and maintain personal desktop firewall.
4. Check for the suspicious network activities of infected computer system mentioned in list and disinfect the same if found.
5. Use only genuine software.
6. Keep up-to-date patches and fixes on the operating system and application software.
7. Exercise caution while opening email attachments.
8. Do not browse un-trusted websites or follow un-trusted links and exercise caution while click on the link provided in any unsolicited emails.
Prerequisites to starting cyber security as career
Before starting career in Cyber Security, you must have the knowledge of web applications, system administration, C, C++. Java, PHP, Perl, Ruby, Python, Computer Networking(basic idea of switches, routers, subnet etc.) and VPN’s, hardware and software (Linux like Kali, Ubuntu OS’s, MS, Apple).
You can divide cyber security in different part:
1)Web Application Security
2)Mobile Application Security
3)IOT
4)Network Security
Different Cyber Security Job Roles
Bug bounty
A bug bounty program is a deal offered by many websites, organizations and software developers by which individuals can receive recognition and compensation for reporting bugs, especially those pertaining to security exploits and vulnerabilities.
These programs allow the developers to discover and resolve bugs before the general public is aware of them, preventing incidents of widespread abuse. Bug bounty programs have been implemented by a large number of organizations, including Mozilla, Facebook, Yahoo!, Google, Reddit, Square, Microsoft., and the Internet bug bounty.
Note: Google has an open forum where, under Vulnerability Reward Program Rules , it has been rewarding any hacker for detecting vulnerabilities in its products since 2010. The winners are also named in its hall of fame.
Penetration tester (Ethical Hacker)
A penetration tester is a type of network security consultant that tries to break into or find possible exploits in different computer systems and software. You can think of them as a type of ethical hacker.
- Chief Information Security Officer
- Security Architect
- Cyber Security Engineer
- Malware Anayst
- Computer Forensic Analyst
Cyber Security Professionals Vs. Hacker
Cyber security professional is to protect the data and systems in the network that are connected to the internet. A hacker tries to find loopholes in a system and break into it. there are three types of hackers:
White hat hacker
White hats are hackers who work to keep data safe from other hackers by finding system vulnerabilities that can be mitigated. White hats are usually employed by the target system’s owner and are typically paid (sometimes quite well) for their work. Their work is not illegal because it is done with the system owner’s consent.
Black hat hacker
Black hats or crackers are hackers with malicious intentions. They often steal, exploit, and sell data, and are usually motivated by personal gain. Their work is usually illegal. A cracker is like a black hat hacker, but is specifically someone who is very skilled and tries via hacking to make profits or to benefit, not just to vandalize. Crackers find exploits for system vulnerabilities and often use them to their advantage by either selling the fix to the system owner or selling the exploit to other black hat hackers, who in turn use it to steal information or gain royalties.
Grey hat hacker
Grey hats include those who hack for fun or to troll. They may both fix and exploit vulnerabilities, but usually not for financial gain. Even if not malicious, their work can still be illegal, if done without the target system owner’s consent, and grey hats are usually associated with black hat hackers.